|
November 13— Congratulations to George Sullivan who successfully defended his thesis today, "Passive Aggressive: Network Attacks via Passive Analysis". Today therefore also marks George's tearful/joyful goodbye to the hygiene server. Congrats George! |

|
October 13— Congrats to Wenyi "Morty" Zhang, Annie Dai, Keegan Ryan, Dave Levin, Nadia Heninger and Aaron Schulman for their amazing CCS paper featured in today's Wired Story "Satellites are Leaking the World's Secrets: Calls, Texts, Military and Corporate Data"! More information can be found at the project page. |

|
| August 13— CSE alumni Stephen Checkoway, Damon McCoy, Danny Anderson, along with Brian Kantor, Hovav Shacham, and Stefan Savage at UCSD together with Yoshi Kohno, Karl Koscher, Alexei Czeskis and Franziska Roesner at UW received the 2025 USENIX Security Test of Time award today for their 2011 paper Comprehensive Experimental Analyses of Automotive Attack Surfaces. This paper, along with its predecessor (which also received the Test-of-time award at IEEE in 2020), is credited with helping to establish the field of modern automotive security. This body of work also received the AAAS Golden Goose Award in 2021. Congratulations to everyone on such an outstanding accomplishment! |

|

|
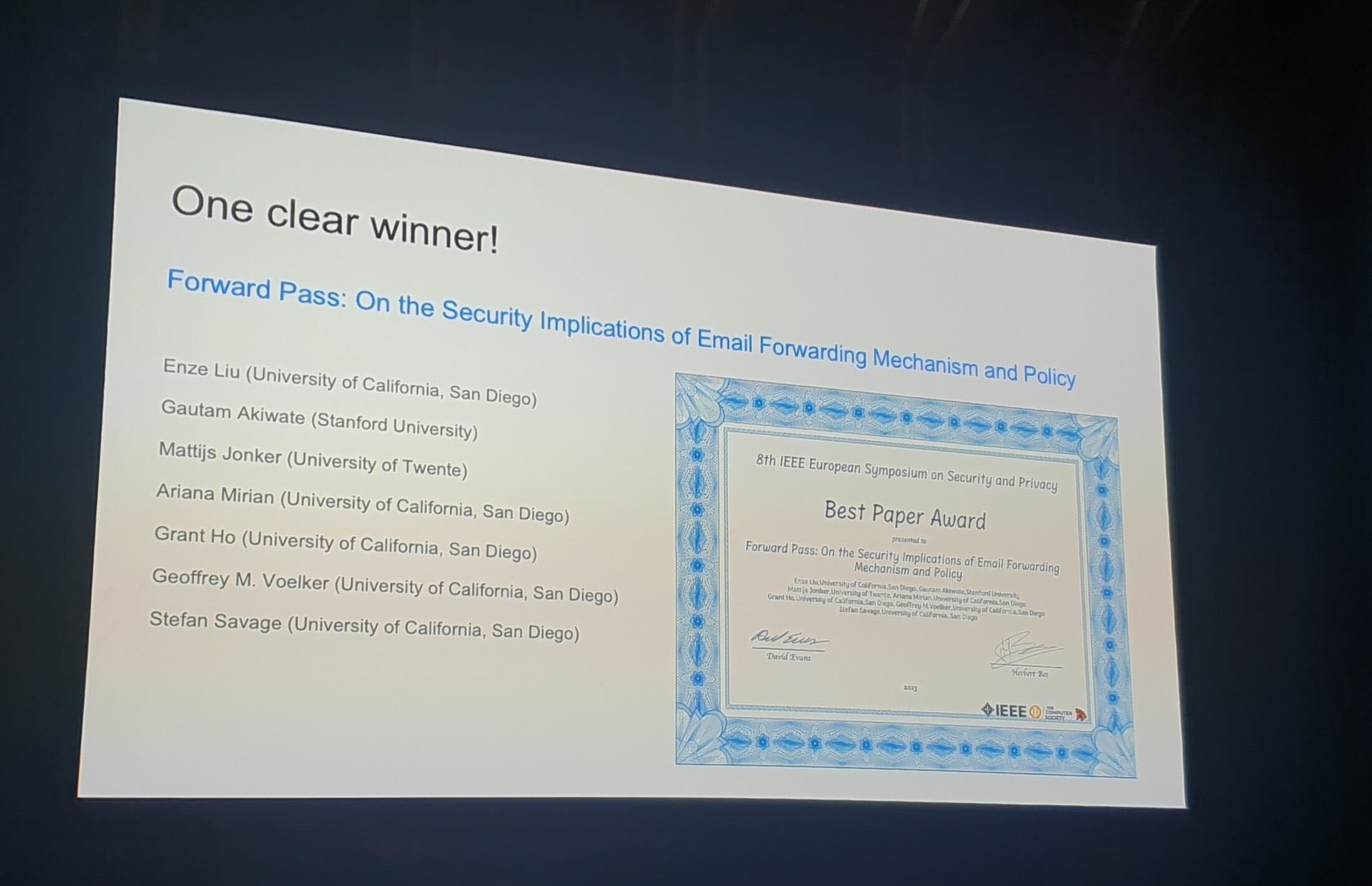
August 11— Congratulations to Enze "Alex" Liu who defended his dissertation today, entitled "Security Vulnerabilities in Service Composition"! Alex has been a cornerstone of the sysnetsec groups, promoting community within the department, supporting and guiding many other students, and blazing trails with his research. Dr. Liu soon transitions to CMU as a postdoc. Congrats, Alex! |
| June 09— Congrats to Keegan Ryan, award-winning storyteller, for defending his dissertation, "Practical Lattice-based Algorithms for Cryptanalysis"! |

|

|
June 04— Congrats to Evan Johnson for defending his dissertation, "Verifiably Secure Software Sandboxing"! Evan came to us from Illinois, refined his inner chill over six years here in SoCal, and is now off to try the other coast as an Asst Professor at NYU. Congrats and good luck Evan! |
| March 17— Welcome home to Hovav Shacham who, after seven years in the Lone Star state, has returned to become part of the UCSD constallation again. Hovav rejoins us officially in July and we're all super happy to have him back! |

|