Using Honeybuckets to Characterize Cloud Storage Scanning in the Wild, Katherine Izhikevich, Geoffrey M. Voelker, Stefan Savage, and Liz Izhikevich,
Proceedings of the IEEE European Symposium on Security and Privacy, Vienna, Austria, July 2024.
Experimental Security Analysis of Sensitive Data Access by Browser Extensions, Rishabh Khandelwal, Asmit Nayak, Earlence Fernandes, and Kassem Fawaz,
Proceedings of the Web Conference (WWW), Singapore, May 2024.
Unfiltered: Measuring Cloud-based Email Filtering Bypasses, Sumanth Rao, Enze Liu, Grant Ho, Geoffrey M. Voelker, and Stefan Savage,
Proceedings of the Web Conference (WWW), Singapore, May 2024.
The Double Edged Sword: Identifying Authentication Pages and their Fingerprinting Behavior, Asuman Senol, Alisha Ukani, Dylan Cutler, and Igor Bilogrevic,
Proceedings of the Web Conference (WWW), Singapore, May 2024.
Practical Obfuscation of BLE Physical-Layer Fingerprints on Mobile Devices, Hadi Givehchian, Nishant Bhaskar, Alexender Redding, Han Zhao, Aaron Schulman, and Dinesh Bharadia,
Proceedings of the IEEE Symposium on Security and Privacy, May 2024.
Architecting Trigger-Action Platforms for Security, Performance and Functionality, Deepak Siron Jegan, Michael Swift, and Earlence Fernandes,
Proceedings of the Network and Distributed System Security Symposium (NDSS), San Diego, CA, February 2024.
On Precisely Detecting Censorship Circumvention in Real-World Networks, Ryan Wails, George Arnold Sullivan, Micah Sherr, and Rob Jansen,
Proceedings of the Network and Distributed System Security Symposium (NDSS), San Diego, CA, February 2024.
Experimental Analyses of the Physical Surveillance Risks in Client-Side Content Scanning, Ashish Hooda, Andrey Labunets, Tadayoshi Kohno, and Earlence Fernandes,
Proceedings of the Network and Distributed System Security Symposium (NDSS), San Diego, CA, February 2024.
An Empirical Analysis of Enterprise-Wide Mandatory Password Updates, Ariana Mirian, Grant Ho, Stefan Savage, and Geoffrey M. Voelker,
Proceedings of Annual Computer Security Applications Conference (ACSAC), Austin, TX, December 2023.
Fast Practical Lattice Reduction through Iterated Compression, Keegan Ryan and Nadia Heninger,
Proceedings of Crypto 2023, Santa Barbara, CA, August 2023. (Best paper award).
When Messages are Keys: Is HMAC a Dual-PRF?, Matilda Backendal, Mihir Bellare, Felix Gunther, and Matteo Scarlata,
Proceedings of Crypto 2023, Santa Barbara, CA, August 2023.
Reductions from Module Lattices to Free Module Lattices, and Application to Dequantizing Module-LLL, Gabrielle De Micheli, Daniele Micciancio, Alice Pellet-Mary, and Nam Tran,
Proceedings of Crypto 2023, Santa Barbara, CA, August 2023.
Error Correction and Ciphertext Quantization in Lattice Cryptography, Daniele Micciancio and Mark Schultz,
Proceedings of Crypto 2023, Santa Barbara, CA, August 2023.
Access Denied: Assessing Physical Risks to Internet Access Networks, Alexander Marder, Zesen Zhang, Ricky Mok, Ramakrishna Padmanabhan, Bradley Huffaker, Matthew Luckie, Alberto Dainotti, kc claffy, Alex C. Snoeren, and Aaron Schulman,
Proceedings of the USENIX Security Symposium, Anaheim, CA, August 2023.
Improving Logging to Reduce Permission Over-Granting Mistakes, Bingyu Shen, Tianyi Shan, and Yuanyuan Zhou,
Proceedings of the USENIX Security Symposium, Anaheim, CA, August 2023.
HECO: Fully Homomorphic Encryption Compiler, Alexander Viand, Patrick Jattke, Miro Haller, and Anwar Hithnawi,
Proceedings of the USENIX Security Symposium, Anaheim, CA, August 2023.
MultiView: Finding Blind Spotsin Access-Deny Issues, Bingyu Shen, Tianyi Shan, and Yuanyuan Zhou,
Proceedings of the USENIX Security Symposium, Anaheim, CA, August 2023.
Understanding the Viability of Gmail’s Origin Indicator for Identifying the Sender, Enze Liu, Lu Sun, Alex Bellon, Grant Ho, Stefan Savage, Geoffrey M. Voelker, and Imani N. S. Munyaka,
Proceedings of the Sympsoium on Useable Privacy and Security, Anaheim, CA, August 2023.
In the Line of Fire: Risks of DPI-triggered Data Collection, Ariana Mirian, Alisha Ukani, Ian Foster, Gautam Akiwate, Taner Halicioglu, Cindy Moore, Alex C. Snoeren, Geoffrey M. Voelker, and Stefan Savage,
Proceedings of Workshop on Cyber Security Experimentation and Test (CSET), Marina del Rey, CA, August 2023.
No Privacy Among Spies: Assessing the Functionality and Insecurity of Consumer Android Spyware Apps, Enze Liu, Sumanth Rao, Sam Havron, Grant Ho, Stefan Savage, Geoffrey M. Voelker, and Damon McCoy,
Proceedings on Privacy Enhancing Technologies Symposium, Lausanne, Switzerland, July 2023.
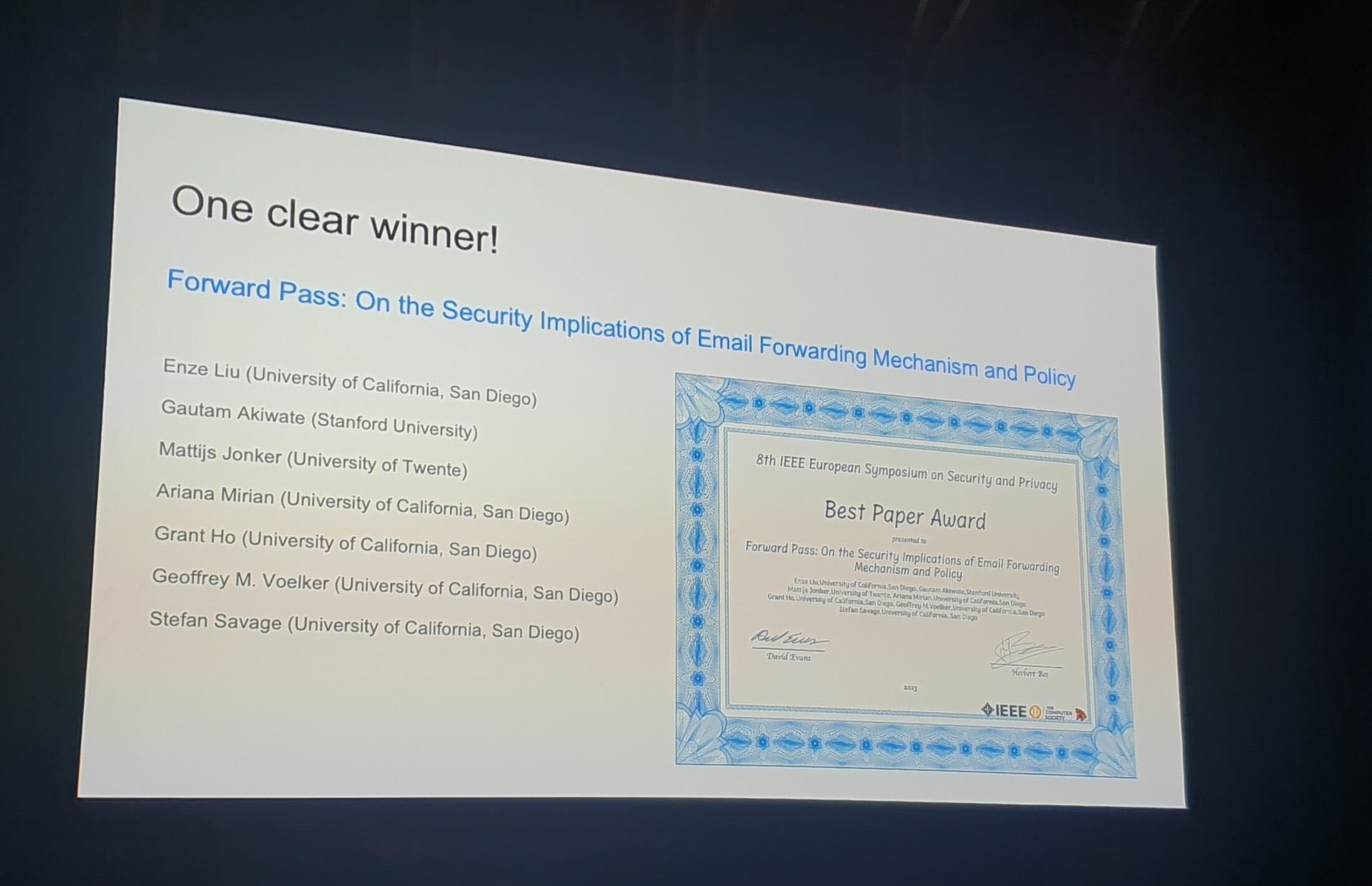
Forward Pass: On the Security Implications of Email Forwarding Mechanism and Policy, Enze Liu, Gautam Akiwate, Mattijs Jonker, Ariana Mirian, Grant Ho, Geoffrey M. Voelker, and Stefan Savage,
Proceedings of the IEEE European Symposium on Security and Privacy, Delft, The Netherlands, July 2023. (Best paper award).
WaVe: a Verifiably Secure WebAssembly Sandboxing Runtime, Evan Johnson, Evan Laufer, Zijie Zhao, Shravan Narayan, Stefan Savage, Deian Stefan, and Fraser Brown,
Proceedings of the IEEE Symposium on Security and Privacy, May 2023. (Distinguished Paper Award).
Half&Half: Demystifying Intel’s Directional Branch Predictors for Fast, Secure Partitioned Execution, Hosein Yavarzadeh, Mohammadkazem Taram, Shravan Narayan, Deian Stefan, and Dean Tullsen,
Proceedings of the IEEE Symposium on Security and Privacy, May 2023. (Distinguished Paper Award).
MEGA: Malleable Encryption Goes Awry, Matilda Backendal, Miro Haller, and Kenneth G. Paterson,
Proceedings of the IEEE Symposium on Security and Privacy, May 2023. (Distinguished Paper Award).
The Hidden Number Problem with Small Unknown Multipliers: Cryptanalyzing MEGA in Six Queries and Other Applications, Keegan Ryan and Nadia Heninger,
Proceedings of PKC 2023, May 2023. (Best Paper Award).
Hardening Signature Schemes via Derive-then-Derandomize: Stronger Security Proofs for EdDSA, Mihir Bellare, Hanna Davis, and Zijing Dai,
Proceedings of PKC 2023, May 2023.
Ransomware Attack Associated With Disruptions at Adjacent Emergency Departments in the US, Christian Dameff, Jeffrey Tully, Theodore C. Chan, Edward M. Castillo, Stefan Savage, Patricia Maysent, Thomas M. Hemmen, Brian J. Clay, and Christopher A. Longhurst,
JAMA Network Open 6(5):e2312270-e2312270, 2023.
Efficient FHEW Bootstrapping with Small Evaluation Keys, and Applications to Threshold Homomorphic Encryption, Yongwoo Lee, Daniele Micciancio, Andrey Kim, Rakyong Choi, Maxim Deryabin, Jieun Eom, and Donghoon Yoo,
Proceedings of Eurocrypt 2023, Lyon, France, April 2023.
Flexible Password-Based Encryption: Securing Cloud Storage and Provably Resisting Partitioning-Oracle Attacks, Mihir Bellare and Laura Shea,
The Cryptographers' Track at the RSA Conference 2023, San Francisco, April 2023.
TagAlong: Free, Wide-Area Data-Muling and Services, Alex Bellon, Alex Yen, and Pat Pannuto,
Proceedings of International Workshop on Mobile Computing Systems and Applications (HotMobile), Newport Beach, CA, 2023.